Security & Safety on TRON
As one of the most popular high-performance public blockchains, TRON is dedicated to building decentralized applications (DApps) and supporting high-throughput transactions. However, with the continuous growth of the TRON ecosystem, network security and anti-scam measures have become increasingly critical.
This guide aims to help TRON users protect their assets and data, as well as avoid cyber threats and scams.
Why Security Matters?
- The decentralized nature of blockchain networks means users must manage assets independently, without the protection mechanisms of traditional financial systems.
- TRON's efficiency, characterized by fast transactions and low fees, fosters a vibrant user community, yet it also creates a fertile ground for scams and hacking attacks.
- As a user, you need to understand how to protect your wallets, private keys, and mnemonic phrases, and learn how to identify and avoid common scams.
Basic Concepts
To build a strong foundation for effective security, it's essential to first grasp these fundamental concepts:
- Blockchain: A decentralized digital ledger that records all transactions and cannot be tampered with.
- TRON: A public chain platform supporting high throughput and low fees, focusing on dApps and stablecoins, such as USDT.
- Wallet: A tool for storing and managing TRON assets, categorized into software wallets, like TronLink, and hardware wallets, like Ledger.
- Private Key: A secret number used to authorize asset transfers from a wallet, which must be strictly confidential.
- Mnemonic Phrase: A set of words used to recover a wallet. If you lose your wallet, the seed phrase can help restore access.
- Self-Custody: Users manage their private keys and mnemonic phrases independently, rather than relying on third-party services.
Understanding these concepts will help you better understand why certain security measures are necessary.
Wallet Security
Your wallet is the gateway to your assets on the TRON network. Protecting it is the first step to security.
-
Choose a Trusted Wallet
- Software wallets: Recommended options include TronLink, Trust Wallet, etc.
- Hardware wallets: Recommended choices are Ledger Nano S/X, ensuring TRON support.
Note: Select well-known and trusted wallet providers, and avoid using unverified third-party wallets. Please refer to the suggested wallets by TRON.
-
Set up Hardware Wallets
- Purchase hardware wallets from official channels, such as Ledger’s official website, to avoid second-hand or unauthorized devices.
- Follow the manufacturer’s instructions to set up the device and create a unique PIN code.
- When generating a seed phrase, ensure it does not reuse mnemonic phrases from other wallets.
- Install the TRON app on the Ledger device and pair it with a software wallet.
-
Protect Your Mnemonic Phrases
- Write down your mnemonic phrases, avoiding digital storage (such as on computers or mobile phones).
- Store copies of your mnemonic phrases in multiple secure locations (such as safes, secure storage in different cities).
- Never share your mnemonic phrases with anyone, including wallet providers or customer service agents.
-
Enable Two-Factor Authentication
- Enable Two-Factor Authentication (2FA) in supported wallets to enhance security.
- Use an authenticator app (such as Google Authenticator) to generate dynamic passwords.
-
Regularly Update Wallets
- Ensure your wallet is always the latest version to benefit from the newest security patches.
-
Use a VPN on Public Wi-Fi
- When accessing your wallet via public networks, use a VPN to encrypt your connection and prevent man-in-the-middle attacks.
-
Test Transactions
- Before transferring large amounts of assets, perform a small test transaction, such as 0.001 TRX, to ensure the wallet is set up correctly.
Smart Contract Security
TRON supports tokens under the TRC-10 and TRC-20 standards, as well as numerous DeFi applications. Users need to understand how to safely interact with smart contracts and DeFi applications.
-
Understand TRC-10 and TRC-20
- TRC-10: Simple protocol-level tokens, similar to ERC-20.
- TRC-20: Complex tokens based on smart contracts, requiring higher security attention.
-
Interact with Smart Contracts Safely
- Always verify the contract address on TRONSCAN to ensure it matches official documents or the project website.
- Check if the contract has undergone professional auditing to confirm its credibility.
- When approving (approve) contract operations, ensure you understand the corresponding content pending approval (such as the authorized amount).
- Avoid interacting with unknown or unverified contracts.
-
DeFi Security Considerations
- Check project credibility: Review whether the project has audit reports, community feedback, and total value locked (TVL).
- Understand risks: DeFi protocols may involve risks such as impermanent loss and rug pulls.
- Exercise caution when providing liquidity or staking: Ensure you understand the protocol rules and potential losses.
- Never connect your wallet to untrusted websites or dApps.
General Network Security
TRON’s unique features (such as Bandwidth and Energy mechanisms) require users to understand how to manage resources and protect network security.
-
Understand Bandwidth and Energy
- On TRON, Bandwidth is required to process ordinary transactions and Energy is required to execute smart contracts.
- Bandwidth and Energy can be obtained by burning TRX or staking TRX; additionally, each address automatically receives a daily allocation of Bandwidth.
- Manage resources: Avoid consuming excessive Bandwidth at once and ensure sufficient resources to execute contracts. If resources are insufficient, transactions may fail, but the resources consumed will not be refunded.
-
Use TRONSCAN to Monitor Transactions
- Similar to Ethereum’s Etherscan, TRONSCAN is TRON’s block explorer.
- Use TRONSCAN to view address activities, transaction history, and contract information.
- Regularly check your address for unusual activities.
-
Protect Private Keys
- Never share private keys or mnemonic phrases.
- Use multi-signature wallets for important operations to enhance security.
-
Cold Storage
- For long-term assets, use hardware wallets or offline storage, such as paper wallets, for cold storage.
-
Network Security Measures
- Use a VPN to protect your internet connection.
- Enable firewalls and intrusion detection systems.
- Regularly conduct security assessments and vulnerability scans.
-
Participate in DPoS Governance
- TRON uses the Delegated Proof of Stake (DPoS) mechanism, allowing users to vote for Super Representatives (SRs).
- Vote for reputable SRs to ensure network security and stability.
- Regularly monitor SR performance to avoid malicious behaviors.
Anti-Scam Measures
Scams are prevalent in blockchain ecosystems, and TRON users should also stay highly vigilant. Please refer to the following methods to identify and avoid scams:
Check Transaction Signature: The Most Critical Security Line of Defense
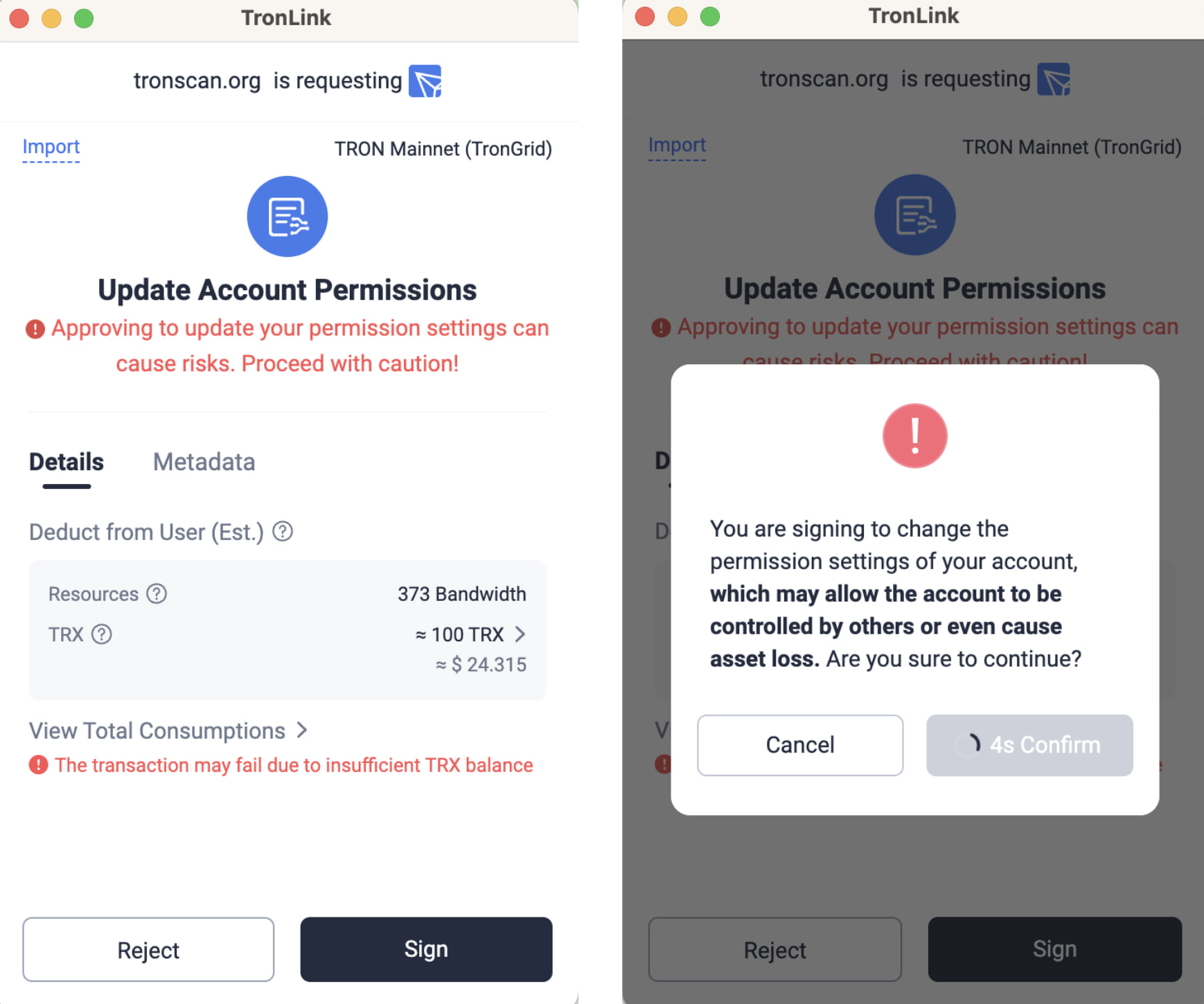
When connecting to dApps, whether a webpage or an application, the most critical security stage is the wallet pop-up request to "sign". Malicious dApps may induce you to sign harmful, unthought-of transactions. Before clicking "Confirm," be sure to carefully read all the content in the wallet pop-up window to ensure that the operation you are about to authorize is completely consistent with your true intentions.
To help users identify high-risk operations, TronLink has built in a powerful security reminder mechanism. When you perform sensitive operations such as modifying account permissions or contract authorization, such as unlimited USDT spending cap, a striking warning window will pop up (as shown in the screenshots below). When you see such a strong reminder, please pause the operation and read every word carefully.
Identify Fake Tokens
- Verify contract addresses: Confirm token contract addresses via Tronscan to ensure they match official documents or the project website.
- Check liquidity: Legitimate tokens have significant liquidity on TRON’s decentralized exchanges (DEXs) like SunSwap. Fake tokens often have drastic price fluctuations due to small transactions.
- Use block explorers: TRONSCAN often marks suspicious contracts as potential scams. Therefore, check token details before interacting.
- Verify website URLs: Beware of phishing websites with slight variations, such as misspelled domains. Bookmark official websites for secure access.
Watch out for Suspicious Patterns
- Fake tokens may mimic legitimate project names or symbols (for example, “TRX2” imitating TRX).
- Airdrops to well-known addresses may create a false sense of legitimacy.
- Fake transfer events or exaggerated metrics are red flags.
Common Scams
- X (formerly Twitter) Phishing: Scammers forge X post link previews to redirect users to malicious websites. Always verify the domain after clicking.
- Giveaway Scams: Promises to double or multiply TRX or tokens sent to a certain address are scams. Never send assets to unknown addresses.
- Compromised Social Media Accounts: Hackers post fake giveaways on stolen accounts. Verify account authenticity before participating.
- Celebrity Impersonation: Impersonating celebrities and KOLs to promote giveaways via live streams or videos is fraudulent. Be skeptical of celebrity endorsements.
- Fake Support Scams: Scammers pose as TRON or wallet support staff to steal private keys. Obtain support only through official channels like the TRON Developer Hub.
- Phishing Scams: Unsolicited emails or messages contain malicious links or attachments to steal credentials or install malware. Avoid clicking suspicious links.
- Fake Crypto Broker Scams: Scammers promise high returns but disappear after receiving funds. Thoroughly verify brokers before investing.
- Unsolicited Airdrop Scams: Unauthorized airdrops may trick users into claiming tokens via scam websites, endangering wallet security. Never interact with unverified airdrops.
If you discover suspicious transactions or scams, report them to TRON official channels or the community immediately.
Continuous Learning and Vigilance
Security is an ongoing process, and users need to continuously learn and update their knowledge.
-
Follow Official Channels
- Stay tuned to the TRON official website, TRON Developer Hub, and community groups (Telegram: https://t.me/TronOfficialDevelopersGroupEn).
- Regularly check official security announcements and updates.
-
Engage in the Community
- Join TRON communities, such as Discord or Telegram, to share knowledge and experiences.
- Report and discuss suspicious activities to help others avoid risks.
-
Learn Security Practices
- Read security guides in the TRON Developer Hub.
- Understand methods to protect private keys, identify scams, and use trusted tools like TRONSCAN.
- Obtain information and support through TRON’s official website, GitHub, or verified X accounts.
- Promptly report suspicious activities to the TRON community or platforms like TRONSCAN to protect other users.
- Stay informed by following trusted sources in the TRON community to understand new scam tactics and security recommendations.
- Learn about security practices from other public chains like Ethereum and Solana to broaden your perspective.
Conclusion
By implementing wallet security, smart contract protection, network security, and anti-scam measures, users and developers can significantly reduce risks in the TRON network. Staying vigilant, regularly updating software, relying on trusted resources like the TRON Developer Hub, and continuously learning about new threats and security practices will ensure your safe operations within the TRON ecosystem.
Updated 4 months ago